Capacity Analysis
How many people are needed within a Security Operation Centre to manage security installations and alerts?
How can security processes be optimised? What actions are needed to respond to regulatory changes? How many people will be needed if the number of connected sites or installations increases? How many platforms to manage alerts? Are the platforms suitable for integrating several or different apparatuses and systems? How to implement systems on the Cloud? How much Cloud is needed to manage video streams? And is the bandwidth sufficient? These, and many more, are the questions our Team of 10459 Certified Analysts, Criminologists and Security Managers answer with Capacity Analysis, i.e. detailed analyses and projects that help companies and organisations manage their security processes from data.
The phases of the Capacity Analysis
The Capacity Analysis carried out by the Secursat Team is aimed at reorganising the workflows of SOCs, facilities, operational centres and more, starting with an accurate assessment of the contexts in which the company operates, the sites and the thousands or even millions of log files produced by the systems, thanks to a data processing model designed by our Team and refined over time. Our approach also reviews the analysis of the platforms in use in operational management and monitoring centres, such as PSIM, VMM, BMS, SCADA and others, analysing their operation and capacity to process data and information, to define the right mix of resources and technologies to optimise the management of processes and digitise repeated and routine ones.
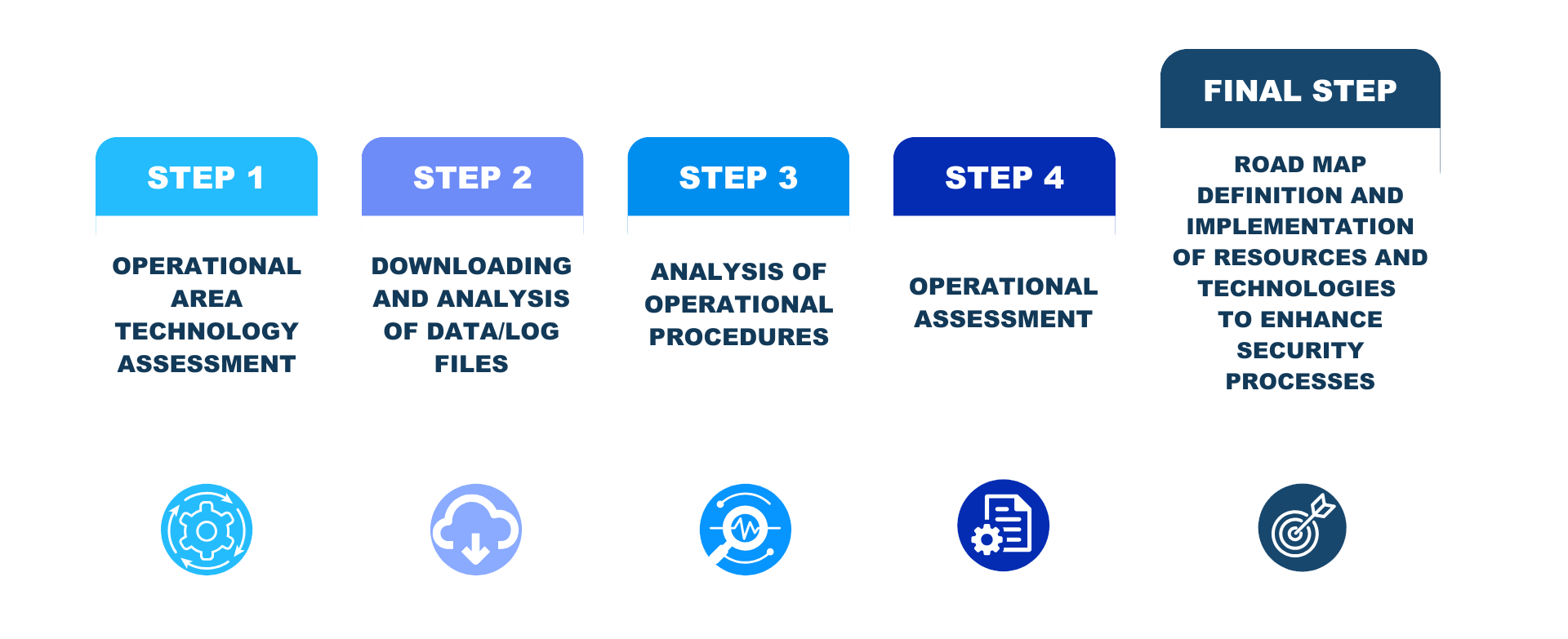
What are the objectives?
Our team's objective is to organise operational security structures to improve process management, the use of internal and external resources, define the skills needed to achieve the desired KPIs, and implement the right technological architecture to respond, not only to today's needs, but also to evolving technological, organisational and regulatory scenarios.
Thanks to our expertise and experience, we develop answers to the needs of regulations such as NIS2 and Dora, and resilient, flexible and scalable security processes, thanks to no-code systems, architectures open to integration and management schemes based on organised data-sets that can be processed from intuitive and simple summary dashboards.
We start with data, often disorganised and not aggregated, to search for useful data and improve the security organisation by following the entire development process.
